In 2019, DE-CIX deployed RPKI at the DE-CIX route servers in order to increase the security of the Internet routing system and support the adoption of RPKI. The adoption was essential to Internet security, and the benefits were visible from day one for all peers and their customers.
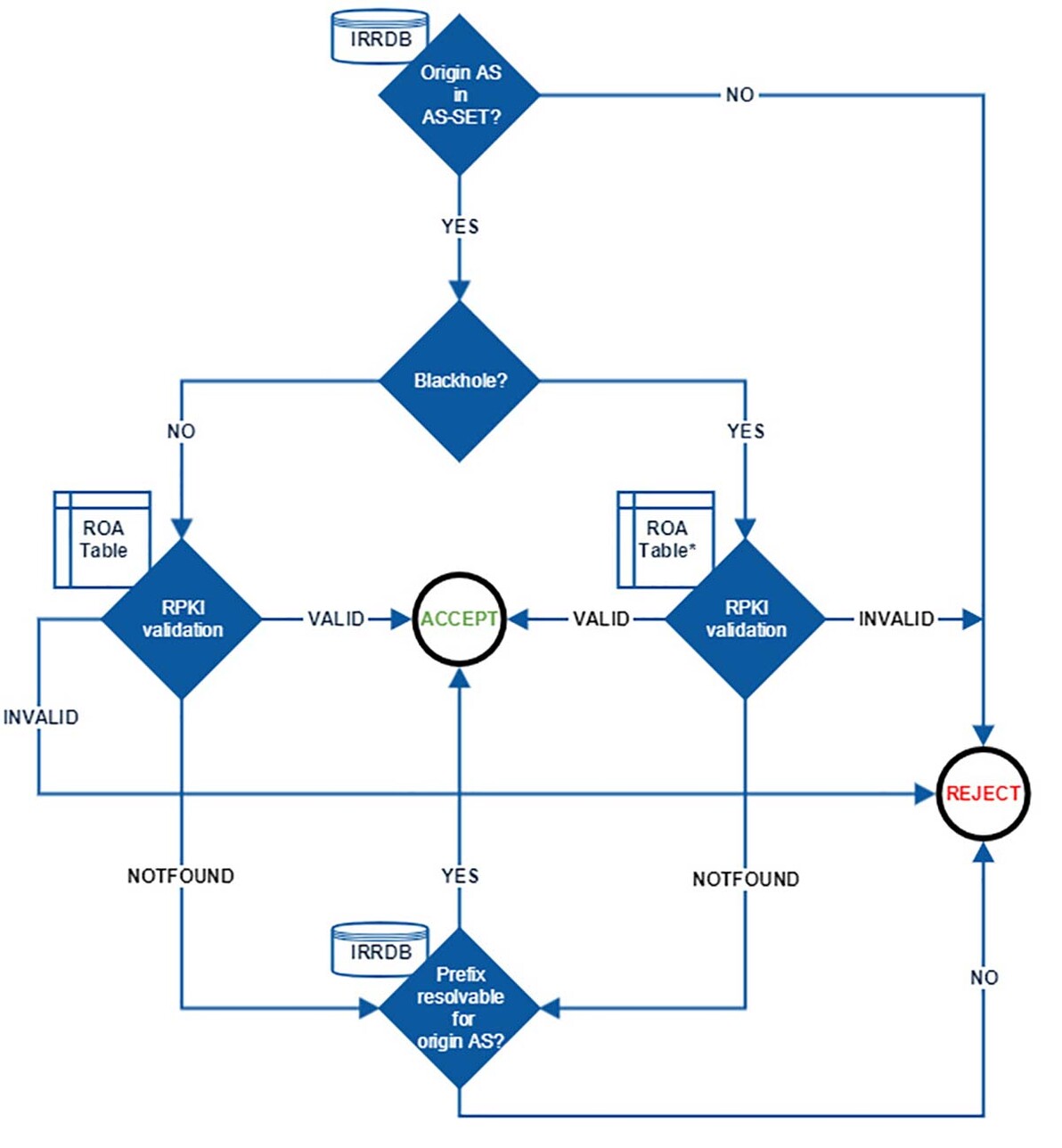
As the combination of RPKI and Blackholing can increase the operational burden, three implementation options were discussed. Option 3 was selected: Strict RPKI origin validation filtering for non-blackholes and loose RPKI origin validation filtering on blackholes.
In the following, you will find some basic information about RPKI and its deployment at DE-CIX. RPKI was implemented at all DE-CIX exchanges except for our exchanges in India, and the exchanges in Berlin, Moscow and St. Petersburg.
If you have any questions, please do not hesitate to contact us.